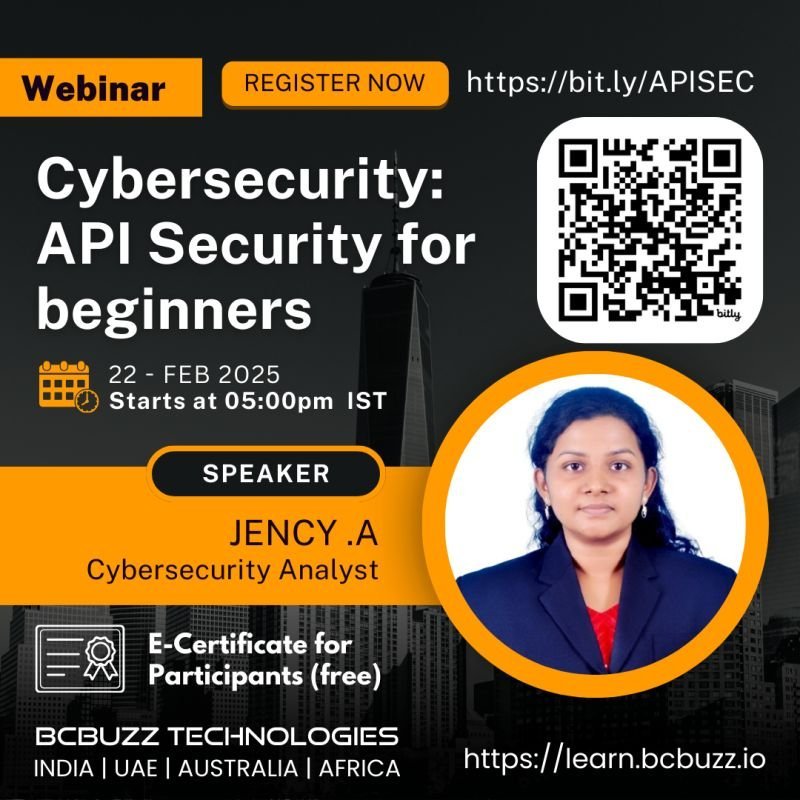
I am deeply passionate about the field of cybersecurity. With hands-on experience in penetration testing and network security, I have developed a strong foundation in identifying vulnerabilities and implementing robust security measures. I have completed training in Ethical Hacking, Cybersecurity, and Web Application Security, and I hold certifications in Penetration Testing, OWASP Top 10 Security Threats, and Cryptography, among others. Currently, I am working as a Cybersecurity Analyst Trainee at BCBuzz Technologies, where I am gaining valuable experience in network security auditing, vulnerability assessment, and ethical hacking. I am proficient in tools like Metasploit, Burp Suite, and Nmap, and I have a strong understanding of network protocols, firewall configurations, and security frameworks.

Badges Earned









Audit Experience
Web App Security
2
Network Security
1
Mobile App Security
1
IoT Security
0
Cloud Security
0
AI & LLM Security
0
Professional Qualifications
| S.NO | CERTIFICATION NAME | ORGANIZATION NAME | COMPLETION DATE |
|---|---|---|---|
| 1 | APISEC Certified Practitioner | APISEC University | 2025, April 22 |
| 2 | Securing API Servers | APISEC University | 2025, April 22 |
| 3 | OWASP API Security Top 10 | APISEC University | 2025, April 22 |
| 4 | API Authentication | APISEC University | 2025, April 22 |
| 5 | API Security Fundamentals '25 | APISEC University | 2025, April 21 |
| 6 | API Documentation Best Practices | APISEC University | 2025, April 15 |
| 7 | Introduction to Hacking Methodology | SimplyCyber | 2025, March 15 |
| 8 | Understanding the OWASP® Top 10 Security Threats (SKF100) | The Linux Foundation | 2025, January 05 |
| 9 | Practical Web Application Security and Testing | The Taggart Institute | 2025, January 04 |
| 10 | Creating with Git | TTI | 2024, December 21 |
| 11 | Pen testing | IT Master | 2024, December 18 |
| 12 | Cryptography | IT Master | 2024, December 10 |
| 13 | Introduction of Cybersecurity | Cisco Network Academy | 2024, December 09 |
| 14 | Networking Basics | Cisco Network Academy | 2024, December 07 |
| 15 | Red Hat System Administration II ( RH134 ) | RedHat Academy | 2024, July 14 |
| 16 | Introduction to MongoDB | MongoDB | 2024, July 11 |
| 17 | Google Cybersecurity | 2024, March 23 |